Responding to Low Severity Security Incidents
Low Severity Incidents are IT security incidents which do not involve a suspected breach of restricted data and have a minor impact on operations. Low severity incidents do not involve the activation of UFIT ISO-CSIRT’s Incident Response procedures. Metrics are collected and reported by the UF Information Security Office.
The UF CSIRT tracks all low-severity incidents using an internally managed ticketing system supported by UF Information Security Office staff. Low-severity incident tickets are automatically generated using event data collected from UF’s intrusion detection systems. As low-severity tickets are generated, email notifications are sent to individuals identified as having either system management or administrative responsibilities for the affected IT asset. Based on feedback provided in ticket updates submitted by system owners or those with management or administrative responsibilities, the incident’s severity and priority are evaluated to determine if the low-severity incident should be reclassified as a high-severity incident requiring an escalated incident response.
Unit IT staff may also discover incidents, such as malware infections, and classify them as low-severity if they do not qualify as a High-Severity Incident. In these cases, there is no requirement to report these incidents to the CSIRT.
Unit IT staff responding to Low-Severity Incident tickets assigned to them by the Information Security Office is to evaluate whether the incident may involve Restricted Data, which would require re-classification as a High-Severity Incident. By accessing the complete ticket using the link provided in the notification email, IT staff should complete the Impact Analysis section and adjust the ticket status based on the results. For instance, if an incident is found to involve Restricted Data, the unit incident responder must change the ticket status to Escalating, in order to alert the CSIRT to the incident. Otherwise, choose the status that best represents the situation. Units are expected to contain incidents the same business day as the notification is sent (or the incident is discovered) and Resolve the incident as soon as possible after that. As an example, resolution of a Low-Severity malware incident typically involves reformatting/re-imaging/re-building the computer and restoring from the last known good backup, and then verifying that the malware is no longer present.
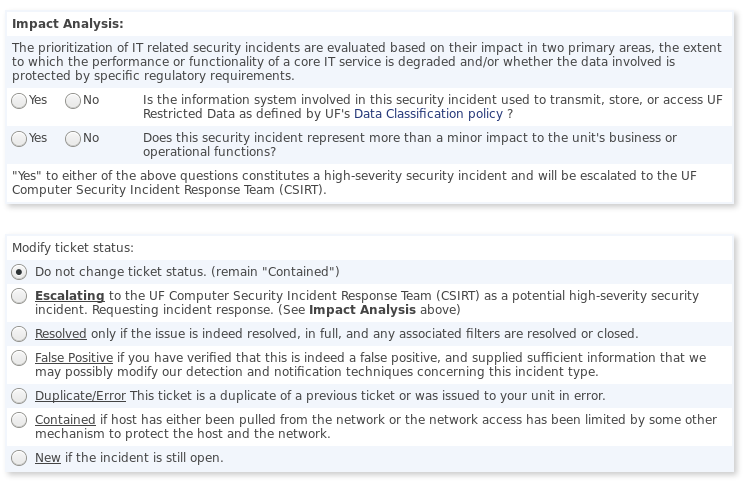
Screen capture from an ISO-generated incident ticket that Unit IT staff are expected to complete.
